You can see its details in the picture below.
The first thing I usually do in these cases is to check if the executable is compressed or not. Some programs pack some of their codes in order to limit our attempt to statically analyze it. To achieve this purpose we are going to use PeID. In the picture below you can see that the program does not detect any compression “Nothing found *”. If the file were compressed with UPX for example, the program would advise us about it and we could uncompress it with this tool.
- Dec 30, 2020 The objective of this paper is to show how to crack an executable without seeing its source code, using the OllyDbg tool instead. Although there are many tools that can do the same thing the beauty behind OllyDbg is that it is simple to operate and freely available.
- Dec 12, 2018 How to crack any software using ollydbg:. Run ollydbg. Open up the program you wish to bypass with ollydbg. Click the play button to run the program with the debugger attached. Right click the CPU window, and click Search For All intermodular calls.
- Ollydbg shows you a lot of data, but for now just notice the Assembly Code in the top left pane, and the Paused message in the lower right. When you load a program into Ollydbg, it starts in a 'Paused' state, with the Assembly Code window showing the first instruction. Running Putty in Ollydbg In Ollydbg, from the menu bar, click Debug, Run.
- Now that you have a cracked the registration protection of this software, launch the software and type any serial number. This should work like charm! Conclusion: This reversing tutorial demonstrates basic reverse engineering concepts using OllyDbg on how to find.
If we click on the “EP Section” bottom, we will see some executable’s details.
2) Use breakpoint-analysis to step through the application and find a serial key from inside the debugger windows 3) Decipher the serial-key generation and create a key-generator to produce infinite product keys. As you can see here is a sample crack-me, “passwordapp.exe”. Upon clicking the application, it shows us to enter a password for.
We can see the R. Size (Raw Size) “400” and the V.Size (Virtual Size) “350” are similar in “.text” . The .text section contains the instructions that the CPU executes and it should be the only section that includes the code. If some day you detect that the R.Size is “0” and the V.Size is “1000” for example, it would be an indicator that the executable is compressed because in the disk it does not have any size (it is packed) and in the memory it has a size (it is unpacked itself).
Now we have the assurance that the file has not been compressed. This is one of the first steps in a static analysis. We are going to make a dynamic analysis with OllyDbg but I want to know if the developer has made an effort in order to try to hide some code. Notice if the executable is packed then we are not going to be able to read a lot of strings within the file. It is possible I will talk about that in future posts...
The next step would be to run the program by double clicking on the executable. After that, we can see that a MS-DOS window is launched and the program requires us to type the serial number. We type a sentence in order to check the program’s behavior.
We have not figured out the serial number… It seems logical…
Now, we are going to run OllyDbg. It does not need installation, just download it and uncompress it. When OllyDbg is opened, just load the executable clicking on File -> Open.
Now we can see the binary code. Don’t worry, remember this post is focused on beginners. We are going to click on the play button in order to run the executable just loaded in our debugger and check the file behaviour.
The program has started and we can see the firsts strings like “Press ENTER to finish”…
(Please, click on the picture to see the entire details)
But… Something happens… The program doesn’t require us to type the serial number like it occurs when we open the application without using a debugger… It’s really strange… It’s like the program knows about our intentions and it is closed by itself when we try to run it with a debugger tool…
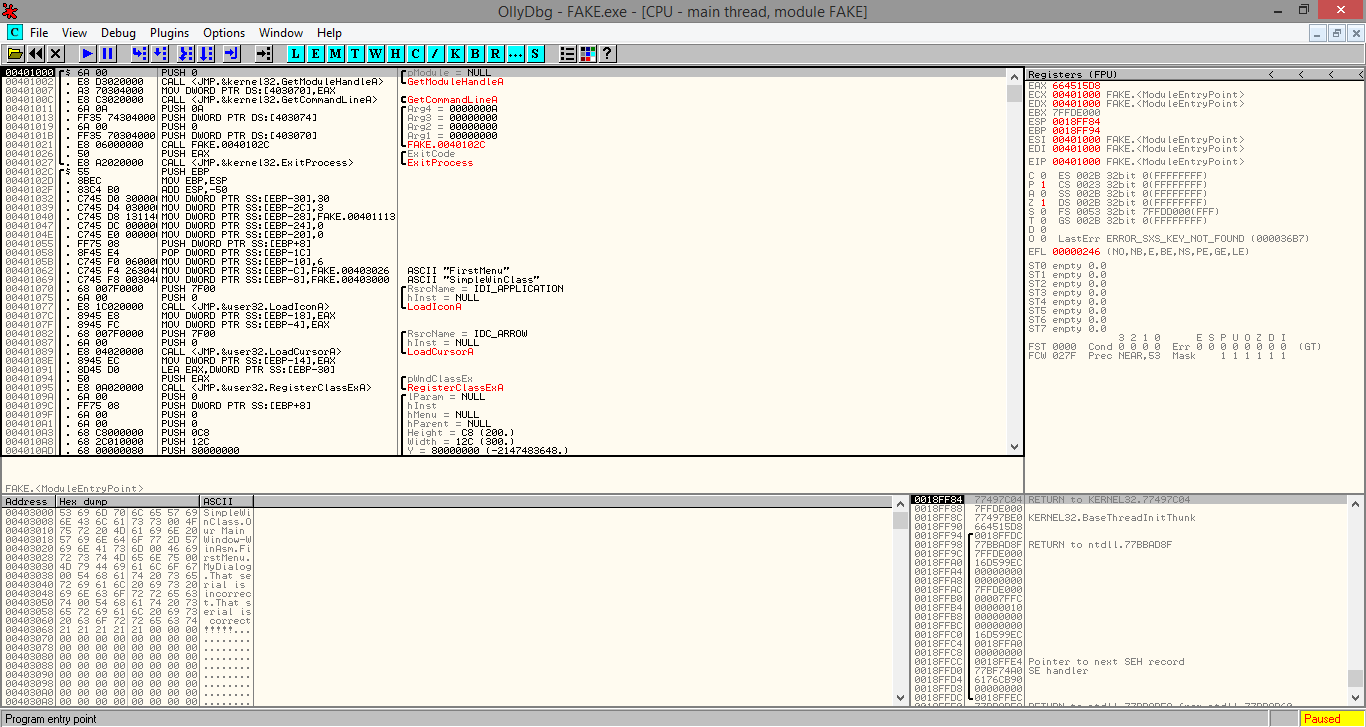
If we reload the file again on OllyDbg, one line of the code draws our attention… The program is calling to the “IsDebuggerPresent” API.
If we seek this API on Microsoft we can see that “This function allows an application to determine whether or not it is being debugged, so that it can modify its behavior”.
Ok, the program is closed when it is open within a debugger. There are many options to avoid being detected by this technique… To achieve this purpose we are going to use the “Hide Debugger 1.2.4” plugin. Just download it and uncompress the DLL in the same OllyDbg’s folder.
It is necessary to restart OllyDbg in order to work with this plugin. If you click on Plugins tab you can see Hide Debugger plugin. You don’t need to do anything else.
We have just installed the plugin to avoid being detected and now, we are going to load and play the executable again. Now the program requires typing the serial number. Great news…
We are going to type a sentence which will be easily recognizable.
If we come back to OllyDbg we can see our sentence in the Arg1.
(Please, click on the picture to see the entire details)
If we continue looking for this sentence through the code we can locate the code below. We can see the String2=”28939387″, the String1=”I’m going to looking for this sentence in OllyDbg now…” and the API call CompareStringA.
We can figure out that the executable is comparing these strings to each other in order for you to check if both have the same value. We can suppose that the string “28939387” is serial number.
(Please, click on the picture to see the entire details)
OllyDbg offers us to copy the value of this line by left clicking on the line we are interested in.
Then, we are going to paste the line’s value to the notepad and then, we are going to copy only the “String2” value: 28939387.
In the end, we just need to try paste the value just copied in our program and… Well!!! We have obtained the serial number of our program!!!
This post could be applied to many of the simple programs which have a keygen integrated but it is needed to have more knowledge if you want to crack more complex programs.
This post is focus on show you some techniques using OllyDbg. It is only a game to get more reversing engineer skills to research malware. Please, don’t contact me to crack programs, it is illegal… I recommend you use to use free software!!!! 😛

You can see its details in the picture below.
The first thing I usually do in these cases is to check if the executable is compressed or not. Some programs pack some of their codes in order to limit our attempt to statically analyze it. To achieve this purpose we are going to use PeID. In the picture below you can see that the program does not detect any compression “Nothing found *”. If the file were compressed with UPX for example, the program would advise us about it and we could uncompress it with this tool.
If we click on the “EP Section” bottom, we will see some executable’s details.
We can see the R. Size (Raw Size) “400” and the V.Size (Virtual Size) “350” are similar in “.text” . The .text section contains the instructions that the CPU executes and it should be the only section that includes the code. If some day you detect that the R.Size is “0” and the V.Size is “1000” for example, it would be an indicator that the executable is compressed because in the disk it does not have any size (it is packed) and in the memory it has a size (it is unpacked itself).
Now we have the assurance that the file has not been compressed. This is one of the first steps in a static analysis. We are going to make a dynamic analysis with OllyDbg but I want to know if the developer has made an effort in order to try to hide some code. Notice if the executable is packed then we are not going to be able to read a lot of strings within the file. It is possible I will talk about that in future posts...
The next step would be to run the program by double clicking on the executable. After that, we can see that a MS-DOS window is launched and the program requires us to type the serial number. We type a sentence in order to check the program’s behavior.
We have not figured out the serial number… It seems logical…
Now, we are going to run OllyDbg. It does not need installation, just download it and uncompress it. When OllyDbg is opened, just load the executable clicking on File -> Open.
Now we can see the binary code. Don’t worry, remember this post is focused on beginners. We are going to click on the play button in order to run the executable just loaded in our debugger and check the file behaviour.
The program has started and we can see the firsts strings like “Press ENTER to finish”…
(Please, click on the picture to see the entire details)
But… Something happens… The program doesn’t require us to type the serial number like it occurs when we open the application without using a debugger… It’s really strange… It’s like the program knows about our intentions and it is closed by itself when we try to run it with a debugger tool…
If we reload the file again on OllyDbg, one line of the code draws our attention… The program is calling to the “IsDebuggerPresent” API.
If we seek this API on Microsoft we can see that “This function allows an application to determine whether or not it is being debugged, so that it can modify its behavior”.
Ok, the program is closed when it is open within a debugger. There are many options to avoid being detected by this technique… To achieve this purpose we are going to use the “Hide Debugger 1.2.4” plugin. Just download it and uncompress the DLL in the same OllyDbg’s folder.
Use Ollydbg To Crack Software Codes Online
It is necessary to restart OllyDbg in order to work with this plugin. If you click on Plugins tab you can see Hide Debugger plugin. You don’t need to do anything else.
Use Ollydbg To Crack Software Codes List
We have just installed the plugin to avoid being detected and now, we are going to load and play the executable again. Now the program requires typing the serial number. Great news…
We are going to type a sentence which will be easily recognizable.
If we come back to OllyDbg we can see our sentence in the Arg1.
(Please, click on the picture to see the entire details)
If we continue looking for this sentence through the code we can locate the code below. We can see the String2=”28939387″, the String1=”I’m going to looking for this sentence in OllyDbg now…” and the API call CompareStringA.
We can figure out that the executable is comparing these strings to each other in order for you to check if both have the same value. We can suppose that the string “28939387” is serial number.
(Please, click on the picture to see the entire details)
OllyDbg offers us to copy the value of this line by left clicking on the line we are interested in.

Then, we are going to paste the line’s value to the notepad and then, we are going to copy only the “String2” value: 28939387.
In the end, we just need to try paste the value just copied in our program and… Well!!! We have obtained the serial number of our program!!!
Download Ollydbg 64
This post could be applied to many of the simple programs which have a keygen integrated but it is needed to have more knowledge if you want to crack more complex programs.
Crack Cracked Software
This post is focus on show you some techniques using OllyDbg. It is only a game to get more reversing engineer skills to research malware. Please, don’t contact me to crack programs, it is illegal… I recommend you use to use free software!!!! 😛
 This post could be applied to many of the simple programs which have a keygen integrated but it is needed to have more knowledge if you want to crack more complex programs.
This post could be applied to many of the simple programs which have a keygen integrated but it is needed to have more knowledge if you want to crack more complex programs.


